Here's a GitHub Action that brings policy checks directly into PR reviews through Overmind's Signals feature. It takes terraform policy violations and displays them alongside infrastructure risk analysis, all in one clean view.
How It Works
When Overmind analyses infrastructure changes, it creates "signals" - indicators about what's happening with your terraform. Things like blast radius, risky patterns, or routine changes. Policy violations fit perfectly into this model.
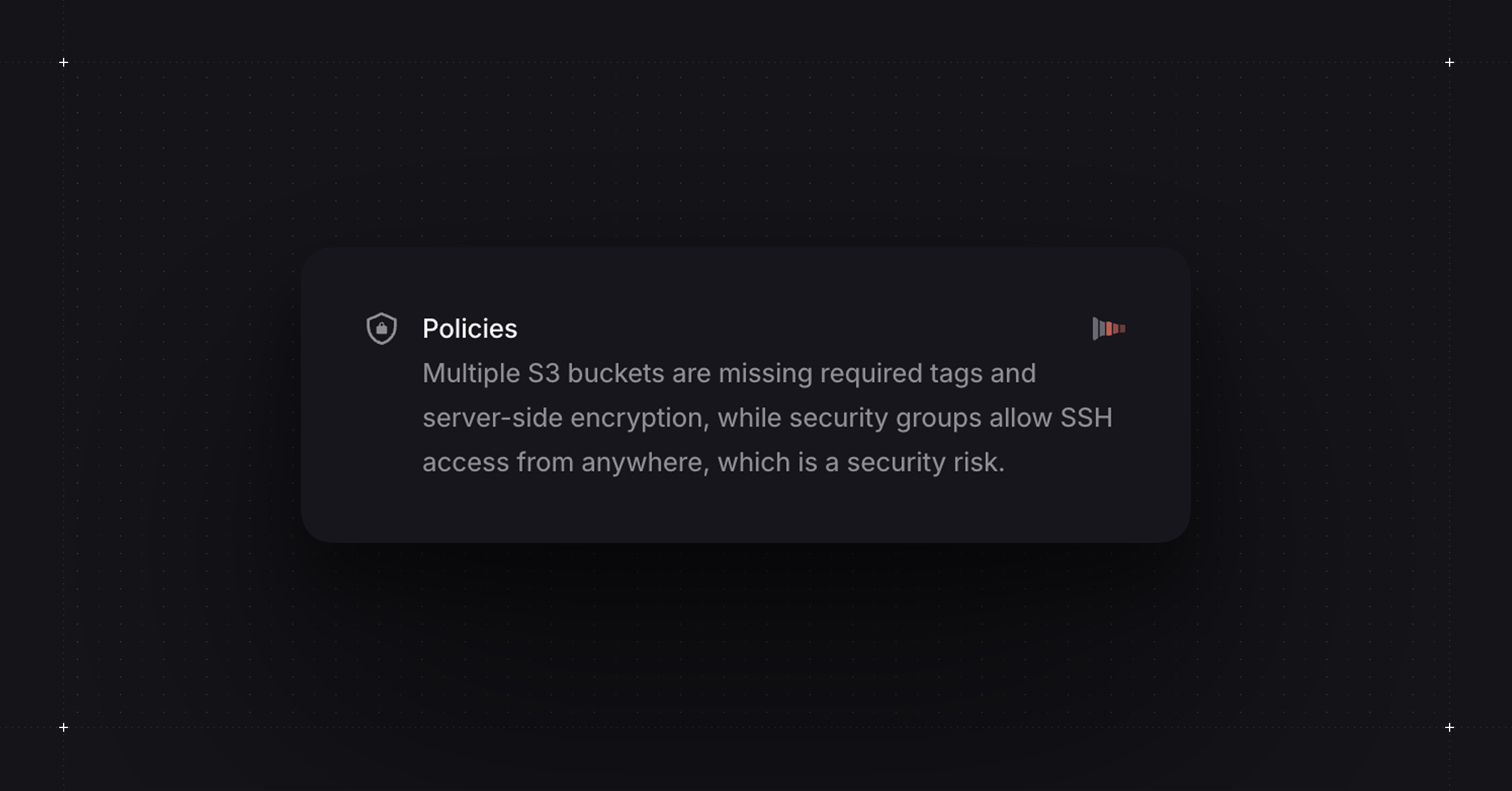
This action runs your OPA/Conftest policies and turns violations into Custom Signals. The result? Policy feedback shows up directly in your PR comment, organized and easy to scan. In the screenshot, you can see "Policies" as its own signal category, listing what needs attention: missing tags, open SSH access, whatever your policies check for.

How This Fits With Your Existing Tools
You might already be using policy tools - Terraform Cloud's Sentinel policies, OPA Gatekeeper, or even GitHub branch protection rules. This action doesn't replace those. Instead, it brings policy feedback into the Overmind context where it can be assessed alongside other risks.
Think of it as adding another lens to your PR review. Your Terraform Cloud policies still run and can block bad deployments. Your branch protection rules still enforce approval requirements. But now you also get policy violations surfaced in Overmind's risk analysis, right where you're already looking at blast radius and change impact.
The difference is context - a missing tag might not be worth blocking a critical hotfix, but seeing it alongside other signals helps reviewers make informed decisions about when to override policies versus when to fix issues first.
Simple Setup
Drop this into your workflow:
- uses: overmindtech/policy-signals-action@v1
with:
policies-path: './policies'
overmind-api-key: ${{ secrets.OVM_API_KEY }}
The action handles the rest - running Conftest against your terraform plan, formatting violations, and submitting them as Custom Signals to Overmind. The screenshot below shows the action and how it submits each policy seperately.

Custom Signals automatically group related issues together. Security violations cluster with security violations, cost issues with cost issues. Instead of a wall of individual problems, you get an organized summary that's easy to review.
It runs in parallel with terraform analysis too. Policy feedback arrives in about 30 seconds while deeper analysis continues. And when all policies pass? Nothing shows up. Clean runs stay clean - no noise.
Writing Policies
The policies are standard OPA/Rego:
deny[msg] {
resource := input.resource_changes[_]
resource.type == "aws_security_group_rule"
resource.change.after.cidr_blocks[_] == "0.0.0.0/0"
resource.change.after.from_port == 22
msg := sprintf("Security group %s allows SSH from anywhere", [resource.address])
}
There are starter policies included for:
- Security basics (open ports, unencrypted storage)
- Cost control (instance type limits per environment)
- Compliance (required tags, encryption settings)
But you'll want to either point it to the correct directory or starting writing your own policies that match your team's specific requirements.
Beyond GitHub
While this is packaged as a GitHub Action, the pattern works anywhere. The core mechanism - submitting policy violations as Custom Signals - adapts to any CI/CD setup. Terraform Cloud users can link signals to run URLs instead of PRs. The Custom Signals API is the integration point.
Try It Out
The action's open source and available on GitHub. If you're using Overmind for infrastructure reviews, it drops right in. If you're new to Overmind, it's a good example of how Custom Signals can enhance your review process.
The goal was simple: get policy feedback where developers actually look - in the PR itself, not in a separate dashboard. Custom Signals made it possible. Each violation becomes a signal, Overmind handles the display and grouping, and it works.
Give it a try and let us know what you think. Policy checks finally appear exactly where they're most useful - right in the PR review.
You can find the Github action repository here.